Getty Images
If you’re using Amazon Web Services and your S3 storage bucket can be reached from the open web, you’d do well not to pick a generic name for that space. Avoid “example,” skip “change_me,” don’t even go with “foo” or “bar.” Someone else with the same “change this later” thinking can cost you a MacBook’s worth of cash.
Ask Maciej Pocwierz, who just happened to pick an S3 name that “one of the popular open-source tools” used for its default backup configuration. After setting up the bucket for a client project, he checked his billing page and found nearly 100 million unauthorized attempts to create new files on his bucket (PUT requests) within one day. The bill was over $1,300 and counting.
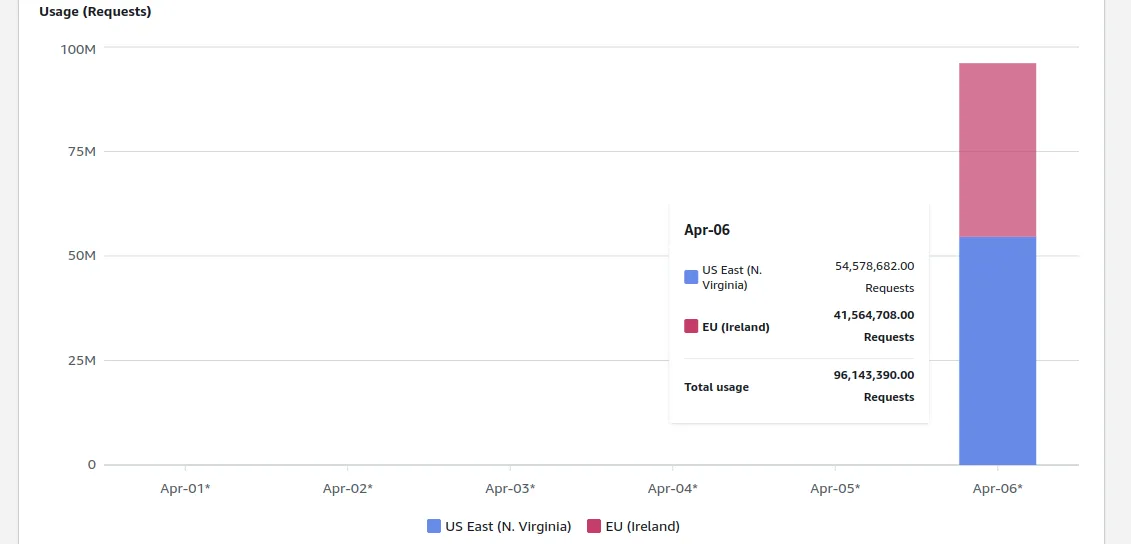
Nothing, nothing, nothing, nothing, nothing … nearly 100 million unauthorized requests.
“All this actually happened just a few days after I ensured my client that the price for AWS services will be negligible, like $20 at most for the entire month,” Pocwierz wrote over chat. “I explained the situation is very unusual but it definitely looked as if I didn’t know what I’m doing.”
Pocwierz declined to name the open source tool that inadvertently bum-rushed his S3 account. In a Medium post about the matter, he noted a different problem with an unlucky default backup. After turning on public writes, he watched as he collected more than 10GB of data in less than 30 seconds. Other people’s data, that is, and they had no idea that Pocwierz was collecting it.
Some of that data came from companies with customers, which is part of why Pocwierz is keeping the specifics under wraps. He wrote to Ars that he contacted some of the companies that either tried or successfully backed up their data to his bucket, and “they completely ignored me.” “So now instead of having this fixed, their data is still at risk,” Pocwierz writes. “My lesson is if I ever run a company, I will definitely have a bug bounty program, and I will treat such warnings seriously.”
As for Pocwierz’s accounts, both S3 and bank, it mostly ended well. An AWS representative reached out on LinkedIn and canceled his bill, he said, and was told that anybody can request refunds for excessive unauthorized requests. “But they didn’t explicitly say that they will necessarily approve it,” he wrote. He noted in his Medium post that AWS “emphasized that this was done as an exception.”
In response to Pocwierz’s story, Jeff Barr, chief evangelist for AWS at Amazon, tweeted that “We agree that customers should not have to pay for unauthorized requests that they did not initiate.” Barr added that Amazon would have more to share on how the company could prevent them “shortly.” AWS has a brief explainer and contact page on unexpected AWS charges.
The open source tool did change its default configuration after Pocwierz contacted them. Pocwierz suggested to AWS that it should restrict anyone else from creating a bucket name like his, but he had yet to hear back about it. He suggests in his blog post that, beyond random bad luck, adding a random suffix to your bucket name and explicitly specifying your AWS region can help avoid massive charges like the one he narrowly dodged.